This is a guest post from Patrick Lambert, security researcher for InfoSec Institute. InfoSec Institute is a security certification company that provides popular CEH and CCNA training.
 Social media is the two-way communication in Web 2.0 and has expanded far past individual use. Social media monitoring and engagement, and social media security for business, have become an essential part of brand management and planning for organizations and it is now commonplace for both individuals and businesses to have accounts on FaceBook, LinkedIn, Twitter and Google+. With the popularity of social media on the rise it is imperative that you keep your sensitive information secure.
Social media is the two-way communication in Web 2.0 and has expanded far past individual use. Social media monitoring and engagement, and social media security for business, have become an essential part of brand management and planning for organizations and it is now commonplace for both individuals and businesses to have accounts on FaceBook, LinkedIn, Twitter and Google+. With the popularity of social media on the rise it is imperative that you keep your sensitive information secure.
Security for Facebook
With around a billion users, Facebook is definitively the most popular social network in the world. It also offers all kinds of features, from your own personal wall, to games, messaging, email and more. As such, it’s no surprise that Facebook accounts are something hackers target on a regular basis. In fact, these accounts are compromised so often that on underground Russian hacker forums, the rate they get sold for is around $2. That’s how much your Facebook account, your past life on the social network, and all your connections, would be worth to a bad guy on the other side of the world. There are many trivial ways for these crooks to compromise a Facebook account, and that’s why you need to take some steps to make sure they won’t get yours.
Some of the ways hackers use to take over Facebook accounts include phishing emails, trying to trick you to log in through a fake Facebook portal, and malware. There are dozens of viruses spreading throughout the net on a constant basis that do nothing but look for unpatched computers, and then take over the social media accounts you log into. This could mean your own account, but for many professionals, it’s often more than one.
If you run your own business, or handle the corporate accounts of the place you work at, you may well be logging into more than one account, and if your computer gets compromised, then all of the accounts could be in danger. Worse, Facebook makes it fairly tricky to gain access back. The way this site works is that if you try to gain access to a compromised account, it will ask you to identify some of your friends. If you have just a few dozens close friends, that may not be too hard. But the truth for many of us is that we often befriend people we don’t know that well, and being shown their current profile picture would not be all that helpful to recognize their name. So it’s best if you can avoid having to go through account recovery altogether.
Thankfully, Facebook offers some features that can be useful to make sure your account is safe. First, the site has geo-ip monitoring software. This means that if you try to log in from a remote location, like say Eastern Europe, the site will detect it and ask additional questions, sometimes even sending you an email. This brings us to a key security feature everyone should know for both Facebook and all other online accounts.
In almost every case, the one most vulnerable part of the whole account login process is the email you use. Everything is tied to that one email address, including what you type in when you log in, and what is used if you try to reset your password or to recover your account. But for most people, their email address is well known. So the first thing to do is sign up with a second, hidden email. Use an address that no one knows about to log into these services, or associate it as a hidden email in the Facebook settings, something you can easily do. That way, if someone tries to log in as you, they will need to know what that secret address is.
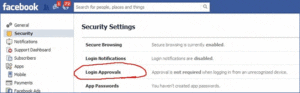
Another feature few people know about is two-factor authentication. Facebook offers a second authentication feature called Login Approvals which is the same thing as Google’s authenticator or PayPal’s token. You can enable it in the security options, and then use the Facebook mobile app on an Android or iOS device to generate a code every time you log in from a new computer. By using these two tricks, you can reduce the chance that your Facebook account will be compromised by a lot.
 Security for Twitter
Security for Twitter
Twitter is probably the second most popular social network out there, and as such it should be kept secure. Unlike Facebook, Twitter offers few features, and that includes on the security front as well. Also, Twitter is something you likely use on a lot of devices, and give access to several apps. If any of these apps is malicious, it could start posting as you, deleting past posts, or even compromise your whole account, depending on how it has access to your Twitter account. While your Twitter presence may not be as important as Facebook, and you don’t have years of photos stored on their servers, getting a large Twitter following can be costly and time consuming, and as such you may want to make sure your account is secure.
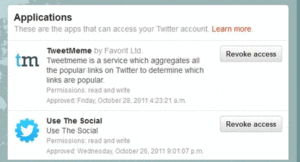
The first thing you should do is make sure the email you associate is also a hidden address, just like for Facebook. Then, go to the Twitter settings on the web site, and check out which apps have access to your account. Twitter, just like Facebook, has a list of apps to which you have granted permission. You should never give your Twitter password to another app or device. You should always make sure they use Twitter’s OAuth API, which is what happens when the app opens a small window from Twitter which asks you if you want to grant them permission. That way, the app will appear on this page, and you can revoke access at any time.
 One more thing you may want to think about for all social media, but especially Twitter, is whether or not you want to use geotagging. On Twitter, the default option when you tweet a photo from a mobile device is to tell the world where you are. Because tweets are open to the public by default, that means anyone can scan the site to find people close by, and then this could in turn put your personal safety at risk. There are scripts out there that scan Twitter for key phrases like “left home” or “gone to the gym” along with geotagging information. It may seem paranoid, but these things exist, and could be a gem for thieves looking for empty houses.
One more thing you may want to think about for all social media, but especially Twitter, is whether or not you want to use geotagging. On Twitter, the default option when you tweet a photo from a mobile device is to tell the world where you are. Because tweets are open to the public by default, that means anyone can scan the site to find people close by, and then this could in turn put your personal safety at risk. There are scripts out there that scan Twitter for key phrases like “left home” or “gone to the gym” along with geotagging information. It may seem paranoid, but these things exist, and could be a gem for thieves looking for empty houses.
Security for Google Plus, and your Google account
Google Plus is the least popular social network, but in a way it may also be your most important account, because that same Google account can be used for so many services. If you use Gmail, Google Docs, Google Reader, Google Plus, and so on, those are a lot of different services you can gain access to with a single user name and password. Here, assuming you use Gmail as your primary contact address, there’s no way to keep your user name hidden, so everything rests on your password, and so it’s key to use a strong password. Your email account, in many ways, is the most important online account out there, because it serves as recovery for all your other accounts.
Fortunately, Google has several features that can help. The first one is two-factor authentication. Google provides an authenticator app on Android and iOS that you can use to login. Of course, this may be annoying if you use many Google services on many devices, but it’s definitely an added security. Also, Google will periodically ask you to confirm a secondary email and phone number. It’s important to add those as well because they can be used in case you lose access to your account. Finally, in the security settings of your Google account, there’s an option that says Always use HTTPS. This forces Google to always revert to a secure connection when you access Gmail or other Google accounts. This keeps the information going from your system to the site secure.
In the end, it’s not hard to keep your online accounts safe, all you need is to make sure you keep your own system up to date, because if you get infected, nothing will protect you, and then make sure you turn on the various security features that these sites offer. With that, you should be fairly certain that hackers would have a very hard time getting into any of these accounts.
Special offer
Lots of marketers don’t know exactly how to use social media to generate leads. Or if they do, they feel like they’ve gotten into the game too late, and there’s nothing they could possibly do now to catch up to their competitors who have already jumped on the social media bandwagon.
But the good news with social media is that once you’ve gotten your bearings and done a little up-front work, it’s not that hard to maintain and continually grow your presence. you just need a plan! And this ebook is going to give it to you. After you read this ebook, you’ll have a social media marketing program that makes your competitors sweat. Frankly, they won’t know what hit them. So tell them to watch out (or better yet, catch ‘em by surprise) … it’s time for you to start your 30-day training regimen for social media domination. Ready? Let’s go!





